Fort Firewall : Version 3.14.8 (Software)
Introduction:
Fort Firewall : Version 3.14.8 (Software). Fort Firewall 3.14.8 is a robust and sophisticated firewall solution designed to offer comprehensive protection to your network and digital infrastructure. Since the threat of hacking, phishing, malware attack, and unauthorized data access has risen over time. And network security is considered the prime concern for every business and individual. Fort Firewall are designed by Fortinet to provide a scalable, efficient. And manageable firewall solution for both small-scale and enterprise-level operations.

Fort Firewall is a high-performance security tool, and the most recent release is version 3.14.8. It offers new functionalities, improved manageability. And enhanced capabilities in the security features that reinforce the defense of your network. It is designed to efficiently handle traffic management, threat detection, intrusion prevention. And VPN support so that the user can help secure the networks from sophisticated online threats.
In this article, we explore in detail the key features, system requirements, and capabilities of the Fort Firewall version 3.14.8 software. And how that helps organizations continue to maintain cybersecurity posture and protected sensitive data integrity.
Description:
Fort Firewall 3.14.8 is an application that belongs to the Fortinet security suite, dedicated to businesses of all sizes. And also targeted at more advanced home users seeking enterprise-level network protection.
You may also like :: TapinRadio Pro : Version 2.15.901 (x64)
It provides a complete set of security solutions that will not only protect the network from inbound and outbound threats but also provide the administrator with fine-grained control over network traffic. Fort Firewall helps the enterprise deploy real-time monitoring, logging, and alerting in order to protect their infrastructure.
Fort Firewall is powered by FortiOS, Fortinet’s proprietary operating system, which introduces several advanced security capabilities. FortiOS ensures that all incoming and outgoing network traffic are analyzed and filtered for possible threats to security, such as malware, denial-of-service attacks, and unauthorized data access. It uses signature-based and behavior-based detection techniques to identify and neutralize threats in real time.
The new advanced features of Fort Firewall 3.14.8 are automatic threat detection, policy-based access control, and creating secure remote access through VPNs. The firewall is designed to integrate seamlessly with other Fortinet products to offer a unified and fortified security ecosystem.
Overview:
It has considered both mature and reliable means for comprehensive purposes of network protection. Be that the defense of external attacks, inshore traffic control-in all these situations, Fort provides effective solutions and secures your business operation accordingly. The supporting software provides almost all the wide-ranged features one administrator may ask while attempting to lock up his total network environment.
Key aspects of the firewall’s capabilities include:
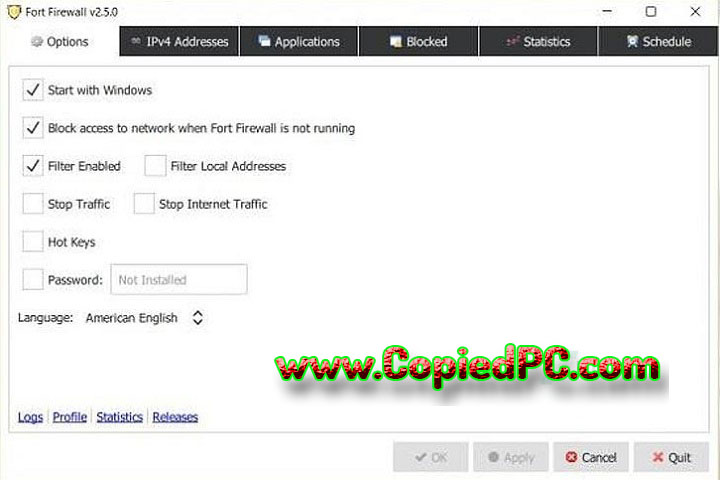
1. Traffic filtering and monitoring
The major function of Fort Firewall is traffic filtering. It will inspect both inbound and outbound traffic to allow only valid network traffic in. Malware, ransomware, and SQL injection are some of the various kinds of cyberattacks. It can block by packet filtering, deep packet inspection, and traffic analysis.
Administrators can also view the real-time traffic. With visualized reports showing the pattern of traffic and potential threats-blocked activity-aids in highlighting weak spots within the network. And optimizing the firewall policies that suit the need of the network.
You may also like :: SmartFTP Enterprise : Version 10.0.3247
2. Intrusion Prevention System (IPS)
Fort Firewall 3.14.8 comes with the most recent Intrusion Prevention System that passively and actively passively scans any incoming and outgoing traffic against known attack signatures. Its capability for pattern detection means this system is able to deny malicious traffic in real-time and block zero-day exploit attempts from trying to permeate to the network. IPS is valuable in the case of an attack that takes advantage of vulnerabilities that have not been hitherto reported by traditional measures.
Overview:
3. Secure VPN Access
Fort Firewall 3.14.8 provides businesses with an easy way to safely connect remote personnel or branch offices to the main network through the Virtual Private Network capabilities of the software. This, in turn, makes it possible for Fort Firewall to allow data transfer between such clients and the network of the organization within an encrypted tunnel. The VPN will facilitate an organizational policy to secure sensitive information against external hackers and adhere to various relevant regulatory requirements pertaining to data security.
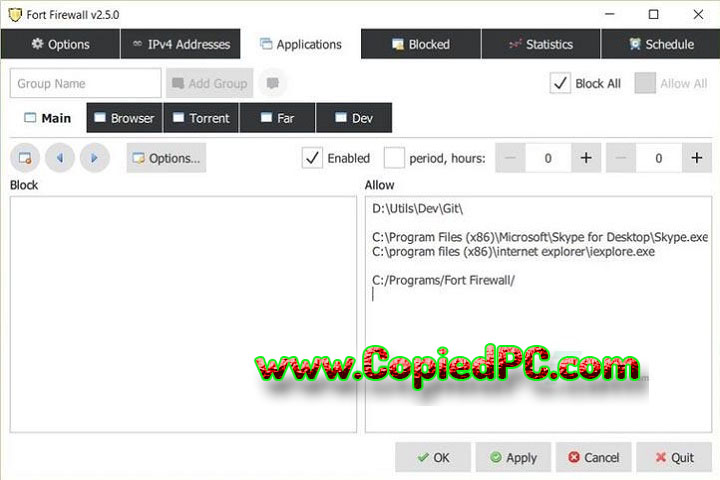
4. Access Control and Policy Management
Fort Firewall performs powerful access control by defining a very granular policy, differentiated between various users, devices, and applications. It defines what kind of traffic is allowed based on source IP, destination IP, time of day, application type, and more. Policies can be defined for explicit use cases like guest access, internal users, or remote workers, ensuring the right people have the right access.
5. Web Filtering and Application Control
Fort Firewall 3.14.8 provides full-scale web filtering, enabling blocking access to malicious websites or inappropriate content. The software configures a URL categorization database for assurance of accessibility to just safe and permitted sites. Accordingly, application control policies could be implemented to restrict applications from running in the case of certain applications that might pose a security risk, like peer-to-peer file-sharing utilities or applications with unknown origins.
Overview:
6. Segmentation of the Network
Network segmentation: Fort Firewall 3.14.8 supports network segmentation, whereby your network aresegmented into different zones for different functions and security measures, making the management and operation of the networks much easier. Thus, Fort Firewall protects against lateral threat movements inside a network by isolating different network parts into zones to prevent lateral threat movements. The possibility of setting policies for every segment apart, observing traffic, and all sorts of security rules helps assure integrity and security for the most sensitive information while minimizing an organization’s attack surface.
You may also like :: Total Commander : Version 11.50
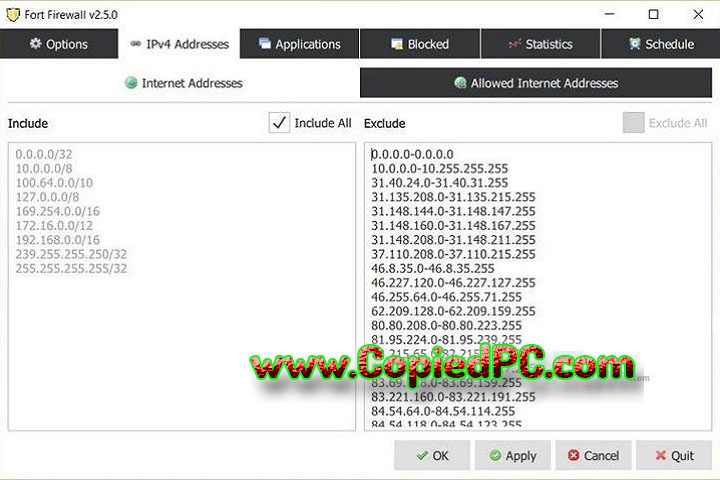
7. Extensive Reporting and Logging
The software provides detailed reports and logs, thus enabling the administrator to trace network activities as well as observe firewall performance. This includes all the allowed or blocked traffic, intrusion attempts, VPN connections, and lots more. All these reports are tres valuable in compliance audits, performance tuning, and security analysis. Fort Firewall supports integration with SIEM systems for advanced threat detection and reporting.
Software Features:
Fort Firewall 3.14.8 boasts several special features that were intended to implement a secure, yet efficient, network environment.
Deep Packet Inspection-DPI: It finds and blocks sophisticated attacks by analyzing packet contents in real time.
Intrusion Detection and Prevention System-IDPS: Actively detects and blocks a wide variety of network-based attacks.
VPN-S: Secure (IPSec & SSL) makes provision for encrypted remote access over the organization’s network to remote workers and branch offices.
Web Filtering and Content Blocking: The technology has the ability to block unauthorized websites and web-based content for an organization to keep browsing secure.
Bandwidth Management: This helps in controlling network traffic and gives priority to the flow of applications according to user requirements, thereby increasing overall network performance.
High Availability: Provides redundancy and failover capabilities to ensure network always-on in case of hardware failure.
Centralized Management: This solution, paired with Fortinet’s FortiManager, is designed to manage such devices centrally for consistent policy enforcement.
Application Control: This allows the administrator to control and view applications running within the network and block suspicious apps that are dangerous.
SSL Inspection: It inspects SSL-encrypted traffic to identify hidden threats in encrypted communication.
Multi-factor Authentication (MFA): It provides more security with a number of verifications a user has to make in order to access the network.
System Requirements:
Fort Firewall 3.14.8 is designed to run on a wide range of hardware platforms, from small businesses to enterprise-level environments. System requirements vary depending on the scale of deployment and the specific role the firewall will play in the network. Below are general system requirements for installing and running Fort Firewall 3.14.8.
Minimum System Requirements:
Operating System: FortiOS 6.0 or later
Processor: Multi-core processor, 2.0 GHz or higher
RAM: Minimum 2 GB
Storage: 10 GB free space for installation and logs Network Interface: At least 2 Ethernet ports VPN: IPSec VPN or SSL VPN to be supported for remote access Recommended System Requirements: Operating System: FortiOS 6.2 and later Processor: Multi-core processor (3.0 GHz or higher) RAM: at least 4 GB Storage: 20 GB available for logs, reports, and system configuration Network Interface: At least 4 Ethernet ports; high-speed connection supported VPN: Dual-mode VPN, allowing multiple users over IPSec & SSL Centralized monitoring and management via either FortiManager or FortiAnalyzer
Download Link : Here
Your File Password : CopiedPC.com
File Version & Size : 3.14.8 | 6 MB
File type : compressed/Zip & RAR (Use 7zip or WINRAR to unzip File)
Support OS : All Windows (64Bit)
Virus Status : 100% Safe Scanned By Avast Antivirus