Tor Browser : Version 14.0.1 (Software)
Introduction:
Tor Browser : Version 14.0.1 (Software). These days, in this digital world, one considers privacy and security very important. Considering that surveillance is always a threat, not to mention hacking and the tracking of data. And quite a number of internet users would prefer ways of browsing safely without disclosure of their identity. Tor Browser 14.0.1 is a powerful tool meant for safeguarding user privacy by relaying Internet traffic. And through multiple random servers, making tracking for any particular user virtually impossible.

Based on Mozilla Firefox, Tor Browser is a fundamental security layer in making users anonymous and keeping them safe on the Internet. It’s great for not getting tracked online, accessing websites that apply strong censorship. And also offers a better way of keeping browsing behavior safe; one could hardly find more trustworthy and workable solutions than Tor Browser. This article has looked at the feature set, system requirements, and finally. The overall benefits this browser offers to enhance online privacy, in view of Tor Browser 14.0.1.
Description:
Tor Browser 14.0.1 is the latest version of this well-liked web browser developed to safeguard each user’s anonymity and privacy online. The Tor Browser is based on a network that is free and open-source, allowing any kind of communication over the Internet to be performed anonymously. It is designed to protect against traffic analysis surveillance by routing internet connections via multiple nodes across the world, thus obscuring users’ IP addresses and encrypting their internet traffic.
You may also like :: Astute Graphics Plug-ins Elite Bundle : Version 3.9.5
A very essential attribute of the Tor Browser is anonymity during Web browsing. It sends the traffic via a decentralized network of relays or “nodes” such that tracking it back to the user is close to impossible by any entity: governments, hackers, and advertisers alike. This anonymity ensures sensitive information about location, browsing habits, and personal data will remain private.
Tor Browser is an open gateway to websites and content not available in many countries. It connects to the dark net, a collection of sites with deeper layers of privacy, hence making it popular with journalists, activists, and people living in restrictive regimes.
Overview:
The Tor Browser works by running your traffic through a series of volunteer-operated servers-named nodes or relays-that encrypt and pass off the data to the succeeding node. In the path that your data reaches after leaving, there would have gone multiple layers of encryption to make tracking impossible by anyone using the origin and destination of such traffic.
This forms a multi-layer encryption that gives the name “onion routing”. Anonymity with Tor Browser can be helpful in many situations.
The other typical use for Tor is in evasion of censorship. It would normally come into place in an instance where a person would like to access a given website or service barred from a certain region. This is so for people living in those countries that do not give too much freedom for unrestricted access to the internet; an example is China and Iran.
Privacy protection: Tor Browser is designed to safeguard your personal information or browsing activity with a cloaking IP address. Most of the time, it is taken into consideration when browsing sensitive websites or performing activities for which privacy is crucial, such as communicating with a journalist or a whistleblower.
Evading surveillance: Tor makes it impossible for hackers, governments, and corporations to track and monitor users’ activities online. Since your IP address is hidden, the browser doesn’t allow malicious parties to collect data about your internet usage.
It is also important to bear in mind, though, that while Tor browser does offer good privacy protection, it is not infallible, and the security you get from using it depends on your usage and the websites visited. For example, it is still not advisable to log into your personal accounts, such as your e-mail account, since this might reveal your identity.
You may also like :: Lightjams : Version 1.0.0.706 (x64)
Software Features:
Anonymity and Privacy
The core feature of Tor Browser is strong anonymity. Traffic routed over the Tor network hides your IP and encrypts your browsing many times over. This makes it almost impossible for anyone, including even ISPs or government agencies, to track your activities online.
Access to the Dark Web
Tor Browser lets one access not only the normal web but also the dark web, where websites are hosted with increased levels of security and anonymity. Such websites are normally accessed via a.onion domain extension and are not indexed by conventional search engines; hence, tracking or censoring them is more difficult.
Bypass censorship:
Tor Browser is a good tool for avoiding censorship from the government or an organization. People who live in countries with strict internet censorship can use Tor to get information about anything they want. Tor easily bypasses firewalls and internet restrictions that deny access to websites.
Free and Open Source:
Software Features:
Tor Browser is free to download and use. As an open-source project, the source code is freely available for any independent security experts to audit and verify the software. This openness enhances the credibility of Tor and ensures. That it is continuously updated and improved by a global community of developers.
No Tracking:
By default, the Tor Browser blocks third-party tracking cookies. Which means that not only will advertisers not know much about your habits, but neither will any other tracker out there. Blocking trackers provides a way for your browsing to be private but anonymous. And leaving less personal data which may be used by these advertisers.
Strong Encryption:
One of the key features of Tor Browser is the use of encryption. Since users’ Internet traffic bounces through several encrypted nodes, data is secured at each layer. This level of encryption means that no interceptor can eavesdrop on sensitive information, such as login credentials and personal details.
Protection against traffic analysis:
You may also like :: Intuit QuickBooks Enterprise Solutions : Version 2024 v24.0 R10
Software Features:
The Tor Browser is engineered in a way that the techniques of traffic analysis cannot reveal anything about a user and his/her activities. The browser purposefully uses a set of obfuscations to render the traffic patterns difficult to analyze or trace back, which would allow people to maintain anonymity.
Cross-Platform Support:
The Tor Browser is available for multiple platforms, including Windows, macOS, and Linux. Such wide support for various platforms means that users can safeguard their privacy across various devices, whether desktops, laptops, or even portable storage.
Security Updates:
Its keeps getting updated about any security vulnerabilities and enhancement in its working. The development team of Tor is very attentive to keeping the security of the browser intact. So that users can confidently browse their information privacies.
Built-in HTTPS Everywhere:
Tor Browser comes with the HTTPS Everywhere extension pre-installed. An extension like that will force websites onto the more secure protocol, HTTPS, rather than the less secure version, HTTP, to better protect data in flight integrity and confidentiality between your browser and a website.
System Requirements:
The Tor Browser is lightweight and efficient, hence available for most modern operating systems. Here are the minimum specifications required to run Tor Browser 14.0.1:
For Windows:
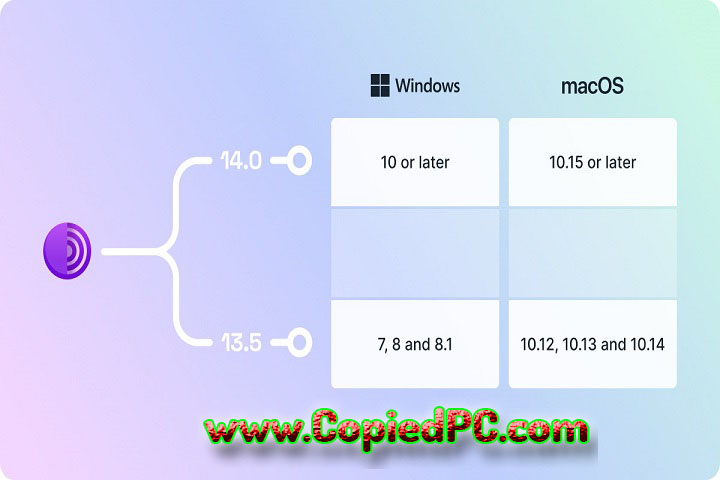
Operating System: Windows 7, 8, 10, 11 (32-bit or 64-bit)
Processor: at least 1 GHz processor
RAM: 2 GB or more recommended
Storage: at least 200 MB of free space
Internet Connection: Required for downloading the software and browsing the internet For macOS:
Operating System: macOS 10.12 or later
Processor: Intel-based processor (Apple Silicon is supported, too)
RAM: 2 GB or more recommended Storage: 200 MB or more free space Internet Connection: for the download of the software and browsing the internet. For Linux: Operating System: Any recent Linux distribution is fine, such as Ubuntu, Fedora, etc. Processor: Processor of 1 GHz or higher speed RAM: 2 GB or more recommended Storage: 200 MB of available space minimum Internet Connection: Required for downloading the software and browsing the internet For Android (via Tor Browser for Android): Operating System: Android 4.0.3 and above Processor : ARMv7 or higher RAM: 1 GB or more recommended Storage: 100 MB available space or more Internet Connection: Must be present to download the application and browse the internet
Download Link : Here
Your File Password : CopiedPC.com
File Version & Size : 14.0.1 | 105 MB
File type : compressed/Zip & RAR (Use 7zip or WINRAR to unzip File)
Support OS : All Windows (64Bit)
Virus Status : 100% Safe Scanned By Avast Antivirus